Cyber News
HackTheBox Writeup – Time



Greetings from Macksofy Technologies. Below is the detailed walkthrough of the Time machine which got retired from HackTheBox
The IP of this box is 10.10.10.214
Port Scan
Running NMAP full port scan on it , we get
We see two open ports , both of them for SSH and Web respectively
Moving towards the Web as always
Way To User
Checking the web, we have a webpage having Online JSON Beautifier and Validator
The Beautify option does the betterment of the JSON code, nothing much to test here
The Beautify option does the betterment of the JSON code, nothing much to test here
Checking the Validate option, we see that it is on Beta version and when testing some JSON code, we get an error and also it shows the library being used in this application ,i.e, com.fasterxml.jackson.databind
After google searches, we see that this functionality is vulnerable and has an active CVE ,i.e, CVE-2019–12384
We are gonna use the exploit and first try to get the ping back to our machine and below you can see what payload , and the file which is helping us to get the ping back
Our ping back was successful, so now we move towards modifying the payload to get reverse shell
We got the shell as user pericles and also we have the user flag as well
Way To Root
Running PSPY, we see that every 30 seconds there is a user created script running which has the privileges to do the stuffs as root as we can see that it is moving the backups to the root folder
Checking the script contents, we can confirm that its running the zipping and moving the backup file to the root folder and checking the file permissions of the script file, we can see it is owned by user pericles and also we can edit the script as well
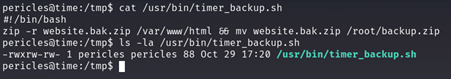
We just use the echo command to put our ssh keys into the ssh folder of the root user
Now after
waiting for few seconds, we try to connect through ssh using our keys and we
get in successfully