Cyber News
HackTheBox Writeup – Academy




Greetings from Macksofy Technologies. Below is the detailed walkthrough of the Passage machine which got retired from HackTheBox
The IP of this box is 10.10.10.215
Port Scan
Running NMAP full port scan on it , we get
We have 3 Open Ports , Port 22 , Port 80 and Port 33060 for SSH , Web and MYSQLx respectively
Looking on the Web part of the NMAP scan, we see it is leading to a redirection towards http://academy.htb domain, so I add it to our hosts file and moving towards the Web
Way To User
Checking the web, we have a webpage where we can see the option for Login and Register
Registering a user and then login
We get a wonderful webpage which is a clone of the HackTheBox’s new initiative Academy
Nothing much in this webpage, so lets check the Gobuster result
We found a admin.php page which redirects us to a login page for admins
We confirmed that the exploit is working for this SaltStack version and now we can get reverse shell through this exploit
We see that the parameter uid is for username , password for password and there is an additional parameter roleid which is by default set to 0 , maybe its for the account privileges on which if we change it to 1 might give us admin privileges
Sending the request and trying to login on the admin.php page redirects us to admin-page.php where we have a page with planner which has some to-do tasks and one of them is still on pending
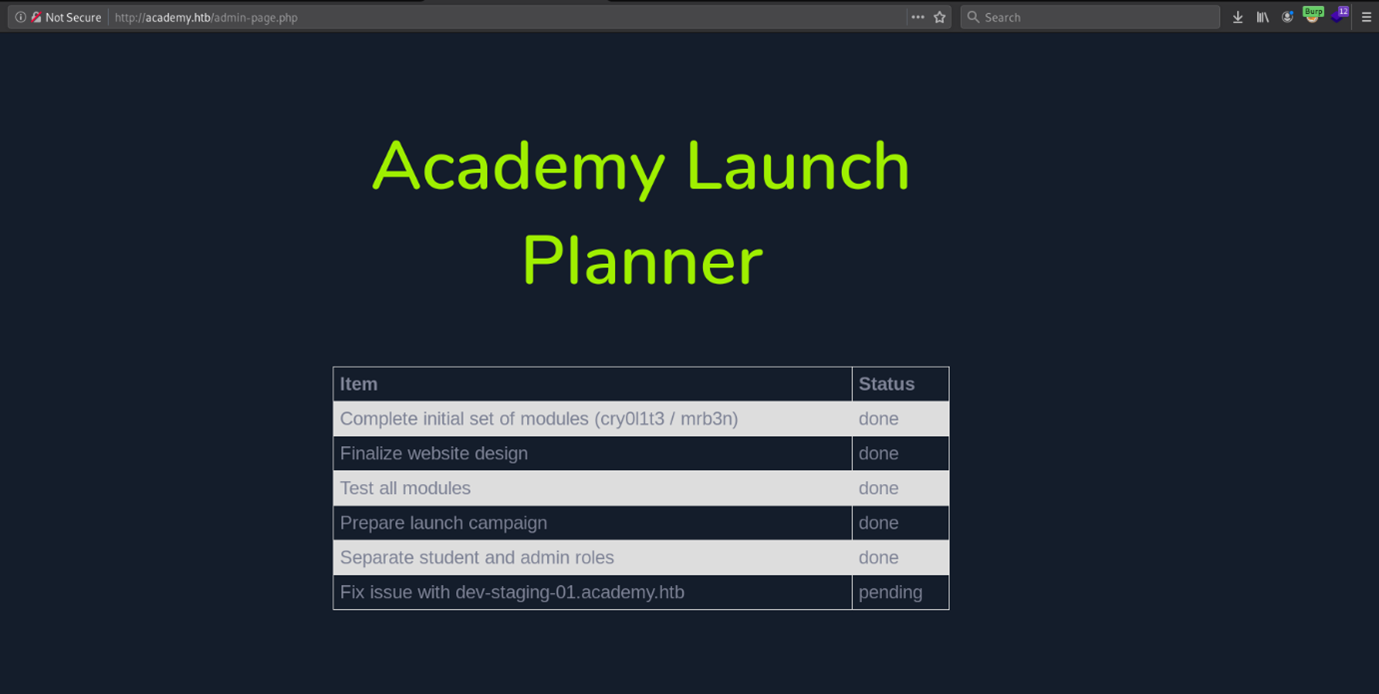
We see one of the task is to fix the issue on the dev-staging-01.academy.htb domain , adding it to our hosts file and trying to access it
Doing some web enumeration on it, we see the Environment Variables which shows the details of the app and it tells us that it is made on Laravel framework
Searching on Google for the exploits on Laravel, we have a exploit available on metasploit
We set the options for the exploit with the required options
Our exploit ran successfully and we got shell as www-data
Enumerating the webroot directory, we have a .env file which has a DB_PASSWORD
Trying the password for the available users on the machine, we get hit successfully on user cry0l1t3
Time for privilege escalation
Privilege Escalation (Way To Root)
Unintended Way
As soon as I was logged in through SSH, there was a broadcast message displayed with the password for mrb3n leaking
Intended Way
Checking the groups of the current user , it is a group member of adm group
Finding files accessible to group members of adm, a lot of logs files were accessible to the current user and interesting ones were the audit log files
Checking those log files, we see that there are a lot of encrypted data
Decrypting all those data using CyberChef’s Magic decryption leads us to the password for mrb3n account
Connecting to the account was successful
Running the sudo -l command, the user can run /usr/bin/composer with sudo privileges
Taking reference from GTFOBins for this binary helped for getting root
References
Insecure direct object references (IDOR) | Web Security Academy
portswigger.net
Offensive Security’s Exploit Database Archive
PHP Laravel Framework 5.5.40 / 5.6.x < 5.6.30 – token Unserialize Remote Command Execution (Metasploit)…
www.exploit-db.com
composer | GTFOBins
It can be used to break out from restricted environments by spawning an interactive system shell.
gtfobins.github.io
Tags: ctf, hackthebox, hard, linux