Cyber News
Hack The Box Writeup – Laboratory




Greetings from Macksofy Technologies. Below is the detailed walkthrough of the Laboratory machine which got retired from HackTheBox
The IP of this box is 10.10.10.216
Port Scan
Running NMAP full port scan on it , we get
We got 3 Open Ports, Port 22 for SSH and Port 80 and Port 443 for Web
Way To User
Checking the NMAP result, we see that the web has redirection to https://laboratory.htb and on the SSL part we see that there is a another domain git.laboratory.htb , so keeping both on our hosts file and checking the web
We confirm from the SSL certificate about the other subdomain
Nothing much interesting on the main domain , so checking the other git domain
We have Gitlab Community Edition installed on the git domain, and we are redirected to the login page where we have options to register a user
We registered a new user and then logged in
Checking the version of the GitLab installed, we see that we have GitLab Community Edition 12.8.1 which has a vulnerability reported on HackerOne for directory traversal
Confirming the exploit by getting the /etc/passwd file
This vulnerability is chained with RCE for which before we have to get the following file
/opt/gitlab/embedded/service/gitlab-rails/config/secrets.yml
Now we followed the report and then create our payload which will be used in Cookie field and for this we have to installed a GitLab instance locally which I did using docker
Our cookie got created and using then ran our curl command and got reverse shell as git user
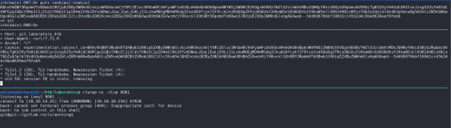
Now we create a new user for gitlab using gitlab-rails console where we assign the admin role to the newly created user
We now login with our newly created user
Login successful and then moving towards finding something interested which were accessible to admins and we had ssh key for the user dexter
We now connect to user dexter through SSH
Way To Root
Checking for SUID binaries, we get an interesting one,i.e, docker-security
Just running the cat command against the binary, we see that the binary is running chmod command where the path is not defined, so we can just hijack the path and exploit it
We exploit the vulnerability and then get root